Top 5 security leaks of Android applications
by Emma Dallas | October 1, 2019 6:18 am
Android Operating System celebrated its 10th anniversary in 2018, and the majority of its users are obviously satisfied with the security policy, as 84% of clients feel safe using this OS. It is hard to disappoint these people, but life is life: 82% of Android devices are subjected to security flaws. Why penetration testing[1] is a must for Android apps and what are their most vulnerable places – go on reading to know.
Penetration testing of Android apps. Key concepts
Android pentesting, as a type of security[2] tests, aims to trace Android vulnerability through simulation of the possible breaches. Its main goals are:
- find app’s weak points;
- ensure the protection of confidential data;
- set up the security policy;
- confirm the company’s reliability.
If you want to reach the set goals and guarantee the software stability, penetration testing should be regular (especially after the Android update). Its basic steps are the following:
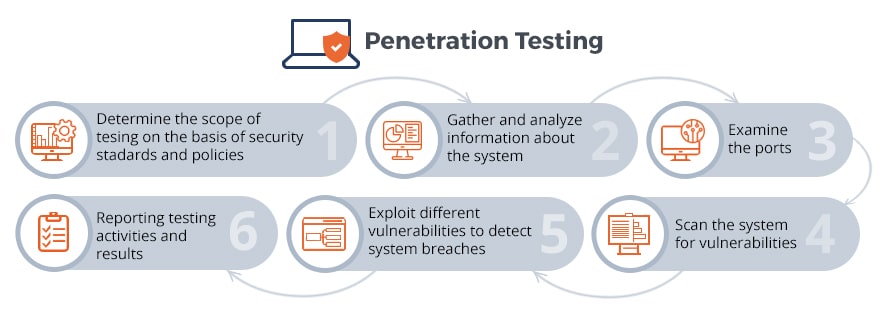
Penetration testing aims to find parts of the software that are most subjected to faults and breaches. Are these parts the same in all types of software? Unfortunately no, but there are definite types of security leaks that are typical for certain kinds of applications. We will analyze Android security leaks.
Main security breaches with steps to check them
Basing on our experience in checking the security of Android applications, QATestLab specialists share their best practices. The table below will give you a description of the functions to check with the required steps, expected results, and comments of our test engineers.
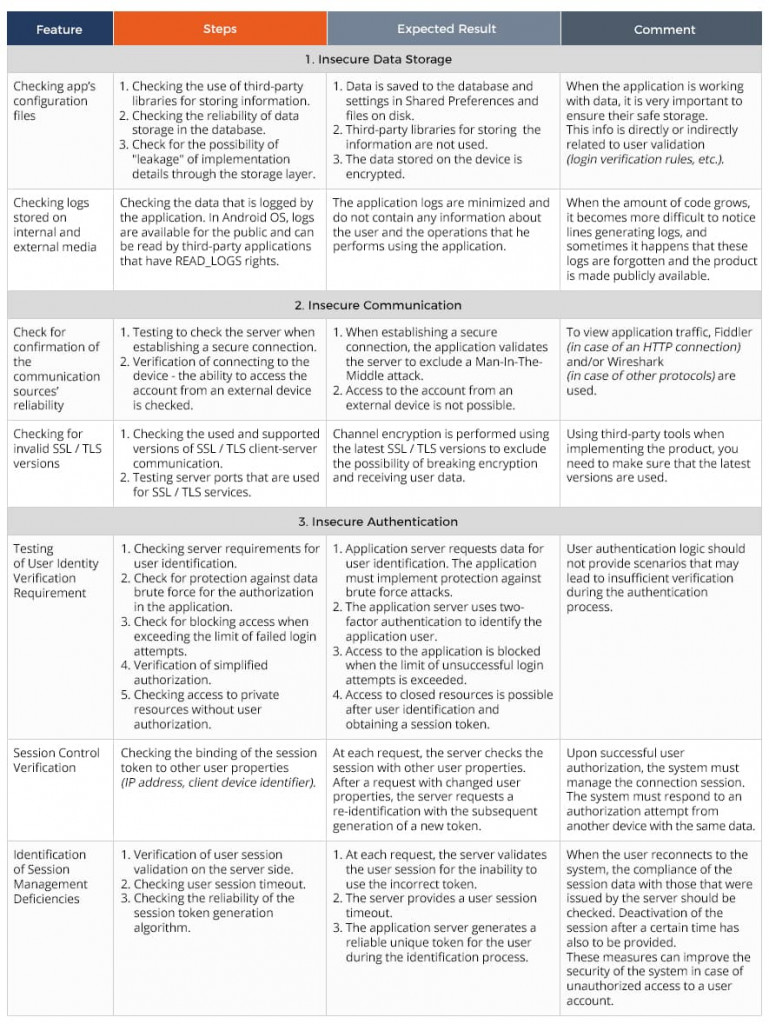
Besides the above-described leaks of Android security as data storage, communication, and authentication, owners of Android apps must take care of such technical issues as cross-site scripting (XSS) and cross-site request forgery (CSRF).
Professional quality assurance[3] of an Android application can mitigate the possible security risks and help meet users’ requirements and expectations. Subscribe to our blog and get more useful advice and unique information.
Learn more from QATestLab
Related Posts:
- penetration testing: https://blog.qatestlab.com/2018/04/30/software-penetration-testing/
- type of security: https://blog.qatestlab.com/2020/09/07/security-testing-types/
- Professional quality assurance: https://qatestlab.com/services/
- Penetration Testing: zero in on security: https://blog.qatestlab.com/2018/04/30/software-penetration-testing/
- How to Select a Penetration Testing Service Provider?: https://blog.qatestlab.com/2017/03/07/penetration-testing-provider/
- 5 Open-Source Mobile App Security Testing Tools: https://blog.qatestlab.com/2017/02/09/mobile-testing-tools/
Source URL: https://blog.qatestlab.com/2019/10/01/android-applications-security-2/

