Blockchain Technology: How Safe Is It?
by Kate Libbie | December 24, 2019 7:30 am
Blockchain technology has made a lot of noise and only the laziest one does not know what it is and how it works. But when blockchain hype subsided a bit, we faced rather serious concerns about its work. These are security matters. Does blockchain coinbase security satisfy all the expectations? Can we trust blockchain today? QATestLab prepared answers to these questions.
The Current State of the Blockchain Coinbase Security
One of the acutest issues with blockchain[1] is multiple misunderstandings around this concept. For this reason, let’s clarify a few key terms.
Blockchain is NOT the synonym for the bitcoin (and cryptocurrency). It is a system, or more precisely database designed to store information. Cryptocurrency is just one of the use cases in the whole gamut, and by the way, it is the most popular one.
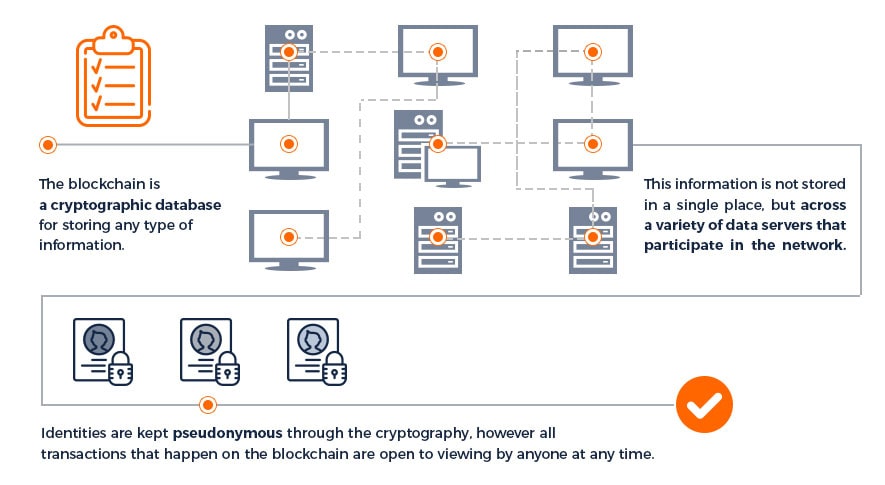
Why do we need blockchain? The technology works like a distributed registry, you can use blockchain for storing any type of information. But the main point is not about storing, it is about providing security[2]. All the data are promised to be hidden from unauthorized persons.
Despite all the sweetest words, there are still places for doubts and skepticism concerning coinbase issues. So why some people believe there’s no good reason to trust blockchain technology? Can bitcoin be hacked?
As practice has shown, there is a considerable amount of blockchain vulnerabilities. The problem is that any participant of the system can gain actual control over the nodes and ownership sharing. An example is the Sybil attack: hackers managed to trick the blockchain by setting false identifiers. Victims were connecting to nodes controlled by intruders and didn’t even know that.
Here are other vivid examples of blockchain hacked scenario:
- March 2014 – Mt. Gox suffered a $473 million loss
- July 2014 – Cryptsy lost 13,000 BTC and 300,000 LTC, which is approximately $ 5.2 million at the current rate
- January 2015 – Bitstamp lost about 19,000 BTC in the amount of $ 5 million
- April 2016 – ShapeShift suffered a 315 BTC loss, which is approximately $130 thousand
- May 2016 – Gatecoin lost total damage amounted 250 BTC ($ 114 500) and 185 000 ETH ($ 1 850 000), in total about $ 2 million
- August 2016 – Bitfinex lost 119,756 BTC, which amounted to about $ 70 million
- July 2017 – Parity Wallet suffered about 153,000 ETH loss, which is approximately $ 32 million
Coinbase security breach is not such a rare event and so this list can go on and on.
The structure of a distributed system of nodes has a rather good protection level. Despite this fact, its auxiliary elements, which are used, for example, when exchanging cryptocurrencies, are protected much worse. For this reason, the security of wallets, exchange procedures and accounts of third-party services cause coinbase security breach scenarios.
Ways to Protect Yourself from Data Breaches
So blockchain is not invulnerable, but the good news is that we can learn ways for protecting ourselves from data breaches. Here things you should do to avoid your account on coinbase hacked:

1. Audit smart contracts
Smart contracts are stand-alone programs that have been hacked many times. An example is the 2016 attack on the DAO, a decentralized autonomous organization and a crowdfunding platform on the Ethereum blockchain. Attackers were able to steal cryptocurrency worth more than $ 60 million. In order not to repeat the sad experience of the DAO, you can use artificial intelligence technology, which allows identifying suspicious activity, as well as scan the code itself to identify known vulnerabilities.
2. Learn quantum cryptography
In the future, cyber defense systems may undergo a significant transformation – the latter will depend on the period of creation, and then the launch of a quantum computer on the market. This prospect forces us to reconsider approaches to ensuring cybersecurity today. Indeed, the possibility of ultrafast computing will allow quantum computer systems to crack almost any crypto code used to ensure the security of confidential data and electronic communications.
On security guard will be quantum cryptography (or quantum encryption), in which information is transmitted using photons. In such a system, it is impossible to grab the information – for this, it is necessary to measure the characteristics of the photon, which will change their state and become a signal about hacking.
3. Buy cyber insurance
One of the problems that every company faces sooner or later remains the difficulty of accurately predicting cyber risks. As a result, investments in cyber defense are increasingly perceived as unjustified spending with an unclear payback horizon. Often this leads to a reduction in even justifiable costs of protection against hackers. The solution for this can be purchasing cyber insurance.
4. Choose open-source code
The risks are great, especially when open source gets into mission-critical enterprise applications. One of the biggest problems remains the publicity of vulnerabilities in the code. Typically, access to such information is freely available to all users for prompt corrections. However, not all companies respond quickly. Open-source software [3]has its advantages. At least “thousands of eyes” are busy searching for vulnerabilities. The probability of their timely detection by “white” hackers is extremely high. Also, such software allows programmers to immediately fix vulnerabilities.
Blockchain Use Cases in Various Industries
Blockchain is developing rapidly not only in the field of cryptocurrencies but also in many other fields. Here are the most popular options for its practical application:
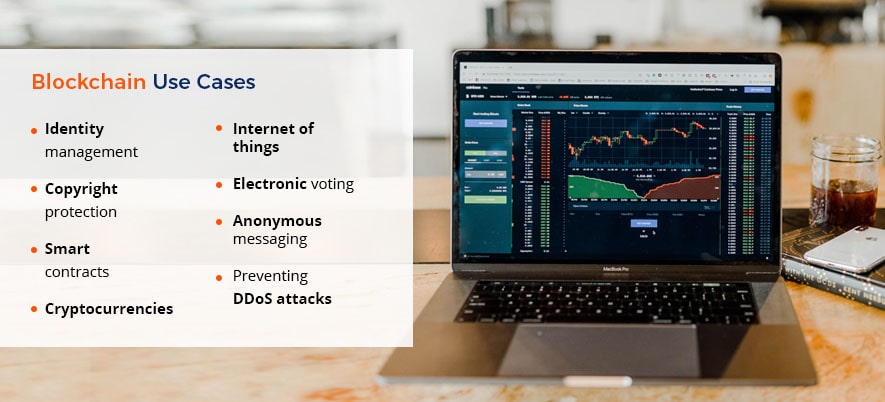
- Identity management. Identity management services allow users to transfer personal data to the blockchain, thus create a digital identity. The user can choose what information can be shared and who exactly can have access to it.
- Copyright protection. The use of the blockchain allows to confirm and protect copyrights and intellectual property rights. Moreover, the technology can ensure the safe storage and prompt updating of information about any object.
- Smart contracts. This type of contract is ideal for use in commercial transactions, as they guarantee the transfer of funds or some other actions as soon as all parties fulfill all the obligations specified in the contract. Smart contracts do not require intermediaries and are executed automatically, which makes them a particularly convenient tool for startups.
- Cryptocurrencies. Blockchain appeared along with Bitcoin, so it isn’t a surprise this technology is used along with a whole range of virtual currencies, the number of which is growing every day.
- Internet of things. The Internet of things (IoT) is a class of devices that can exchange any kind of data among themselves, thereby creating an interaction network. Using a blockchain can guarantee the safety and integrity of data in IoT.
- Electronic voting. Blockchain allows conducting an absolutely transparent electronic voting system. For this, citizens log in to the system and vote using an internal coin. The blockchain records the transaction, automatically creating a register of votes that will be counted at the end of the voting.
- Anonymous messaging. Startups like Obsidian use blockchain technology to secure information in chats, messengers and social networks. Unlike WhatsApp and iMessage, which use end-to-end encryption, Obsidian uses a blockchain to ensure confidentiality of user metadata, such as mail, phone numbers and more.
- Preventing DDoS attacks. Such projects allow users to monetize the unused bandwidth of their Internet networks, combining them into a decentralized CDN (Content Delivery Network). Due to its high bandwidth, the network reflects DDoS attacks, and users can connect to secure protection pools.
What about the future? Well, the blockchain will be especially useful in the field of IoT, artificial intelligence, healthcare, finance, data storage, social networks, document management and more. In addition, there will be more unusual applications like drones delivering food.
Conclusions
To step into the blockchain jungle or not – the choice is yours. Given a sober look for things, there is much more hype than value. If you want to reap benefit from blockchain, then you should clearly understand whether you actually need it. To protect yourself from possible risks, use the blockchain consciously and also remember ways of protecting yourself from data breaches.
Have something to add? Feel free to give your opinion in the comment section below. Visit our blog to learn more about the latest trends in the world of technology and Quality Assurance / Quality Control processes.
Learn more from QATestLab
Related Posts:
- blockchain: https://blog.qatestlab.com/2017/11/28/bitcoin-blockchain-mining/
- security: https://qatestlab.com/services/test-automation/penetration-testing/
- software : https://qatestlab.com/resources/case-studies/software-development/
- Blockchain Testing in 2020: Ultimate Checklist & Tools: https://blog.qatestlab.com/2020/08/04/blockchain-testing-in-2020/
- Testing Blockchain Transactions With Cryptocurrency: https://blog.qatestlab.com/2024/09/26/testing-blockchain-transactions-with-cryptocurrency/
- The Secret of NFT Games Popularity: Features and Benefits: https://blog.qatestlab.com/2022/07/13/nft-games-features-benefits/
Source URL: https://blog.qatestlab.com/2019/12/24/blockchain-technology-security/

