- QATestLab Blog >
- QA Basics >
- Types of Software Testing >
- Security Testing >
- 7 Types of Security Testing
Nowadays, software users are highly concerned about the security of the data they store online. At the end of the day, there is a high possibility that hackers would try to steal it.
This is why cybersecurity is a de facto standard for organizations that value their reputation and customer trust.
What is security testing?
The security assessment is one of many different types of software testing. It enables validating security across all layers of the software and detecting system loopholes.
Software security tests are indispensable whenever significant changes are made to systems or before releasing new applications into a live production environment. It is also crucial to integrate security testing into the product development lifecycle and retest the product periodically.
There is a globally recognized awareness document that lays the foundation for software security. The OWASP Top Ten is a list of the most critical cyber vulnerabilities that may lead to system failures and exposure of sensitive data. Modern security testing methodologies are rooted in guidance from the OWASP testing guide
What are the types of security testing?
- Vulnerability scanning
- Security scanning
- Penetration testing
- Risk assessment
- Security auditing
- Ethical hacking
- Posture assessment
Vulnerability scanning
This type of security testing involves the detection of system vulnerabilities through automated software. Vulnerability scanners examine web apps from the outside to identify cross-site scripting, SQL injections, command injections, insecure server configuration, etc.
The drawback of vulnerability scanning is that it can accidentally cause a system crash if mistakes for an invasive activity.
Security scanning
Security scanning aims to assess the general security level of the system by detecting weak points and loopholes. The more intricate the system or network is, the more complicated the security scan has to be. It can be done as a one-time check, but most software development companies prefer performing security scanning on a regular basis.
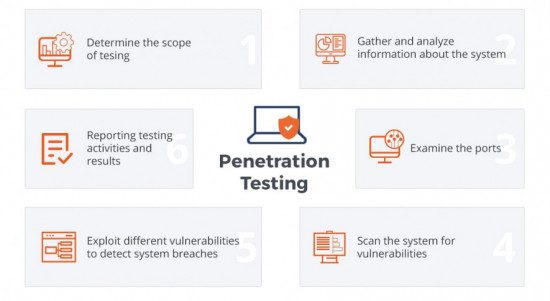
Penetration testing
Pentesting is the imitation of a cyberattack to check for exploitable vulnerabilities. The two most common forms of penetration testing are application penetration testing that aims to detect technical vulnerabilities and infrastructure penetration testing which examines servers, firewalls, and other hardware.
Risk assessment
A security risk assessment is a process of identifying and implementing key security controls in software. It also focuses on preventing security defects and vulnerabilities. A comprehensive security assessment allows organizations to create risk profiles for networks, servers, applications, etc., assess their criticality regarding business operations, and apply mitigating controls based on assessment results.
Security auditing
Security auditing is the process of testing and assessing the security of the company’s information system. A security audit allows verifying the adequacy of the implemented security strategy, uncovering extraneous software, and confirming the company’s compliance with regulations.
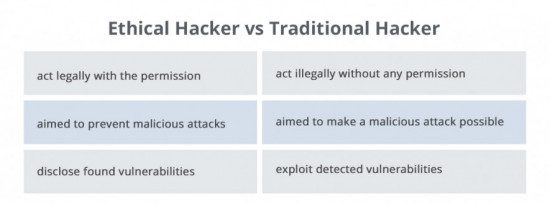
Ethical hacking
The term “ethical hacking” stands for the act of intruding into the system to detect vulnerabilities before a malicious attacker could find and exploit them. Ethical hackers may apply the same methods and tools used by their malicious counterparts but with the permission of the authorized person – they are also expected to report all the vulnerabilities found during the process to the management.
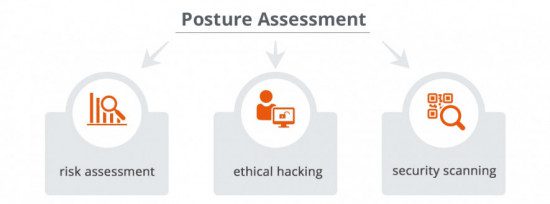
Posture assessment
A cybersecurity posture indicates how resilient the information security environment is when it comes to cybersecurity, and how well the enterprise can defend itself against cyberattacks. Posture assessment provides an overall view of the organization’s security posture, what gaps currently exist, and what steps need to be taken to for improvement.
Conclusion
There is no one-size-fits-all solution with software security – except for regular testing. Leverage this opportunity to demonstrate to your customers that data security is your priority.
QATestLab offers a combination of advanced methodologies and an experienced team able to assess the security of web applications, web services, and mobile applications using the latest tools and techniques. Learn more about why every enterprise needs security testing on our website.








Security scanning is a good tool
123
whats the difference between vulnerability scanning and security scanning?
Security scanning usually includes compliance
Vulnerability scanning is a part of security one.
Vulnerability scanning is automated check of a software against known vulnerable patters.
Security scanning is aimed to assess the general security level of the system.